| Travel Europe blog Computer Tips |
List of Translation
Agencies |
Protecting Your Computer
|
If you get a virus, you should not be overly confident that
your virus protection software will find it or remove it. Many viruses
masquerade as necessary Windows files and hide deep in the root of your system's
brain, undetected by your protection software.
 As one expert quoted:
As one expert quoted:
A disturbing trend in the type of infections we are seeing is the use of "injection" techniques. This involves one or more files injecting themselves into other Windows processes. Once this is accomplished, these type infections generally hide themselves not only from the user, but also from most Security related programs.
Furthermore, viruses are being mutated and created so fast these days that the anti-virus companies can barely keep up with them when trying to create the appropriate anecdotes. And even if they could, it still requires you to download the anecdotes (update definitions), run a system-wide scan to find any virus, and hope the software can remove them.
It is much better to protect your system and know what you are doing so that you do not catch the virus in the first place. Sort of like wearing a sweater and regularly taking Vitamin C to not catch a cold, as opposed to bombarding your system with garlic soup and antibiotics once you have caught it. This page explains how to accomplish this.
Point by Point Procedure for Overall Computer Protection:
-
First, perform a system-wide scan of your computer to make sure it is completely clean of viruses or adware:
-
NOD32 is highly rated and you can download a trial version for free, good for one month. After running a free scan I personally uninstall it, because I am confident my system is secure, I know how not to catch a virus (explained below), and I prefer not to have such software using up
.jpg) unnecessary resources, which may slow down my computer. In any case the
software does not use as much resources as other such programs (such as
Norton or Panda) and is exceptionally good because it works at the
kernel, underlying root brain of Windows, which many others do not.
There are other well-rated and free software such as
Avast or
AVG, if
you want something permanent, but in the past I've been told by users of
some of these that either my email or some of my webpages contained a
virus, which I knew for a fact did not, so these programs could
incorporate bells and whistles to falsely scare you and make you feel secure with them.
unnecessary resources, which may slow down my computer. In any case the
software does not use as much resources as other such programs (such as
Norton or Panda) and is exceptionally good because it works at the
kernel, underlying root brain of Windows, which many others do not.
There are other well-rated and free software such as
Avast or
AVG, if
you want something permanent, but in the past I've been told by users of
some of these that either my email or some of my webpages contained a
virus, which I knew for a fact did not, so these programs could
incorporate bells and whistles to falsely scare you and make you feel secure with them. -
Super Anti Spyware and others is good for ridding your system of spy and adware (the more the merrier as some catch others miss), which is different than a virus. These can be caught just by visiting an infected website.
-
Otherwise, if you feel that your system is so infested and impossible to manage to the point of being unsalvageable, you could always consider a fresh resinstallation.
-
-
Once you've completely cleaned your computer, protect and immunize your browsers so that you do not catch spyware again.
-
Now immunize your email program and learn about bad file extensions (the three letters after the dot at the end of every file name and which reveal what file type it is).
-
Now lock down and immunize your entire Windows and learn how to monitor it for anything suspicious
-
Once you are done with all these, you can test your system to see how secure it is against hackers.
-
Once you are confident you have a beautiful and clean system, back it up.
-
And once you've cleaned, secured, immunized and backed up your system, you might be interested in some tricks on how to speed it up and turn it into a true power horse!
|
|
Introduction: New Threats in the Virus World
Gone are the days when you only had to
 worry about files
attached to emails. The new viruses download to your computer, completely
without your knowledge, simply by you viewing an infected website. Some websites
are infected even without their owner’s knowledge, because they have been
hijacked by these criminals. Once these viruses install themselves on your
computer, they can monitor the keystrokes you punch in on your keyboard ("keyloggers",
such as this freely available
software), and
every website that you visit. So if you log into your bank and punch in your
username and password, this information can be sent out to the virus owners.
Furthermore, these viruses are mutating at an ever faster rate, like the
viruses you find in nature, because they are made freely available on the net
for other criminals, with packages and explanations how to modify them. Hence
they get mutated enough so that they are no longer recognized by the standard
virus protection software, such that the companies selling such software can
barely keep up with creating the necessary definitions to protect you.
worry about files
attached to emails. The new viruses download to your computer, completely
without your knowledge, simply by you viewing an infected website. Some websites
are infected even without their owner’s knowledge, because they have been
hijacked by these criminals. Once these viruses install themselves on your
computer, they can monitor the keystrokes you punch in on your keyboard ("keyloggers",
such as this freely available
software), and
every website that you visit. So if you log into your bank and punch in your
username and password, this information can be sent out to the virus owners.
Furthermore, these viruses are mutating at an ever faster rate, like the
viruses you find in nature, because they are made freely available on the net
for other criminals, with packages and explanations how to modify them. Hence
they get mutated enough so that they are no longer recognized by the standard
virus protection software, such that the companies selling such software can
barely keep up with creating the necessary definitions to protect you.
One expert worded it well:
A few years ago, I would have told you to simply install AVG Free AntiVirus, Spybot Search & Destroy, and Kerio or ZoneAlarm Free, possibly setting Ad-Aware SE aside for a follow-up. This is not nearly enough anymore. Even Kerio (now Sunbelt), with some of the finest inbound exploit protection a personal firewall can offer, free or paid, is still vulnerable. And most of the old, classic scanners are doing little to nothing against the new surge of blended threats, combining the strengths of multiple families of malware which at one time could have been easily distinguished from one another. These mutated parasites can prove much harder to hunt down than their predictable ancestors, as well as harder to remove. And there's more to it than that.
According to Google, more legitimate Web pages are now infected with drive-by downloading keyloggers (http://en.wikipedia.org/wiki/Keystroke_logging) than ever before. With increasing numbers of people taking their finances online, tech-savvy thieves have found it much safer to rob individuals from behind a computer and a proxy tunnel, than to try robbing a physical bank and making their getaway before the wailing of sirens surrounds them. Web rating tools remain useful to advise of a site's trustworthiness, but no longer can you expect not to get infected just because your SiteAdvisor button is green.
It is therefore no longer enough to simply rely on a single piece of software for your complete protection. Rather than fight the symptom once you've caught your virus, it is better to build up your defenses and prevent any virus from infecting your system. Furthermore, much of this software is free (or at least they offer a free, functioning version) and altogether they often use up less system resources than the single, all-in-one yet bloated software which tries to cover all bases. Read further to find out how.
Immunize Your Browsers
Once you feel you have thoroughly cleansed your computer (point 1 at the top), before you get back online and start surfing, you should lock down your computer to prevent ANYTHING from getting back into it.
And obviously the first place you might start is with your browser. Such as set it so that it does NOT automatically download and install cookies.
 MS IE (Internet
Explorer):
MS IE (Internet
Explorer):
Tools > Internet Options > under the Security tab you could choose either Medium-High or High security level for the Internet zone. You could then press on Trusted Sites, followed by the Sites button below that to manually copy in your banks’ https:// address. Note that https is the secure version of http, which is for regular websites. https is used by banks etc. I do not believe you can even copy an http site into this Trusted Sites area.
Now go to the Privacy tab, where I have chosen the Medium setting, which blocks cookies from automatically installing on your computer. But I generally only use IE for certain websites that do not work properly on Firefox, because IE is much more vulnerable to attack. You should probably choose a higher security setting if you regularly surf with IE, and once again, you can manually add cookies to certain sites by pressing the Sites button below the security slider.
In Firefox:
Tools > Options > “Accept cookies from sites” should NOT be activated. If you want to add a cookie from a site, such as your bank’s or email account’s website so that you do not have to repeatedly punch in your username and password, you can copy the domain of your bank (such as bank.com from the address http://login.secure.bank.com) and paste it into the box once you press the Exceptions button next to the “Accept cookies from sites” tickbox.
Before starting this manual procedure though, you should probably erase all the cookies you already have there, making sure to start from scratch and only add those cookies you regularly use or need. Note though that many websites will not even work properly unless you install their cookie, and once you do install their cookie, you should press Refresh (F5 – refresh the page) and then try again. Obviously you should consider carefully before accepting the cookie and make sure you trust the site. Or research about it on the internet if you are not sure.
Under Tools > Options, click the Security tab and select the first three, such as “Tell me if the site I’m visiting is a suspected attack site”. Use your logic, go through the Advanced menus of any browser you are using, and give it good protection.
To further protect your Firefox browser, you might try a search for “ads spy” through the Get Add-ons button through the Add-ons menu. It is nice to see such spamming attempts, as shown here below. The search results from “ads spy” showed five add-ons which looked quite useful and received high user ratings. Pimp up your Firefox!
If you use any other browser, such as Google Chrome or Opera, you should peruse the menus and follow the same cookie-protection and security logic. Most browsers are designed safer than IE (Microsoft Internet Explorer), but IE simply runs better for certain script-heavy sites.
You should then run Spybot and Immunize your browsers. You can also go to the Advance menu mode of Spybot and peruse that, where you will find interesting tweaking tools and tips how to properly set up your browsers (especially IE).
Once you have set up your browsers for safer browsing, you should download and install the modified hostfile. The hostfile lists websites which Windows is instructed to block ANY browser from visiting. The default Windows hostfile is empty, while the hostfile from this site contains a long list of websites recognised as downloading malicious software to your computer in the background. You should therefore download an update of this file occasionally. If there are some websites you still insist on visiting but which are blocked because of this hostfile, you can open the file (found in C:\WINDOWS\SYSTEM32\DRIVERS\ETC\) in Notepad and manually remove such a website from the list (or put a # character at the start of the line). But note that some of the software suggested on this page (WinPatrol) actually blocks any changes to this hostfile, so you may have to fiddle with this. Once you do successfully change the hostfile you need to restart your computer for the changes to take effect.
Another good form of protection is Sandboxie. Sandboxie is a free program (paid for a more robust version) which essentially creates a sand box or fortress around any program you run through it. Such as a browser. You can even run a virus through Sandboxie but which will not affect other and vulnerable parts of your computer because it cannot escape the fortress or area it was designated to (as shown in the pictures below). Therefore, if you run your browsers through this program you can rest assured that no website you visit could damage your computer.
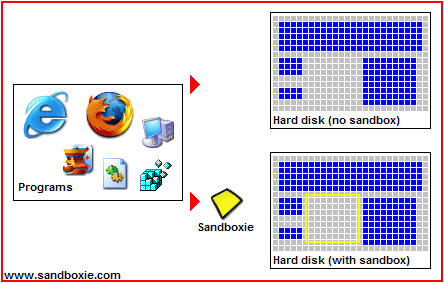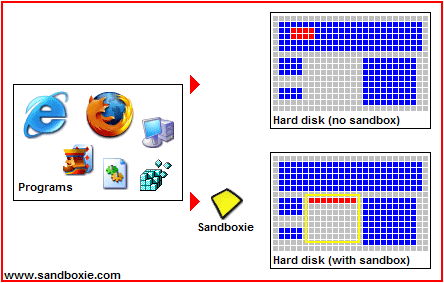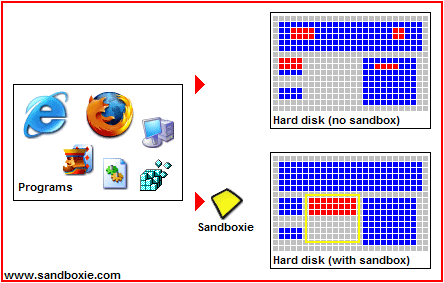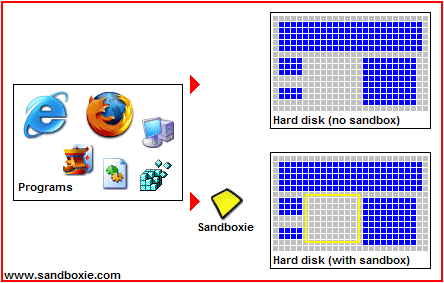
If you're more advanced in computer knowledge you can also try HiJack This: an excellent tool which helps to protect your system against uninvited software. HiJack This will analyse your system and offer a comprehensive log of installed software, startup items and registry keys etc. Reading the logs requires a good understanding of the system, though fortunately there are some very helpful forums where some very knowledgeable people are willing to help.
If you use either IE or Firefox, McAfee's SiteAdvisor can inform you (refer to below picture - green check mark or red cross) which sites have been rated as safe or unsafe (although there is a risk that a site first reviewed as safe has since then been compromised by a third party). Haute Secure is also good because not only does it subscribe automatically to various standard blocklists, it also plugs you into a community of custom blocklists courtesy of other members (unfortunately this service may no longer be free).
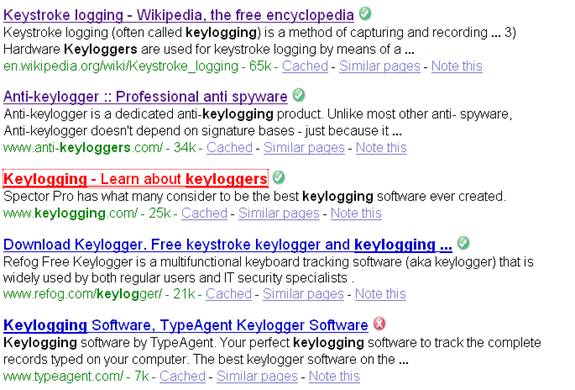
What a search might appear like using SiteAdvisor.
|
|
Lock Down and Immunize your
Windows
What better defense of your system than to build a fortress around key areas to prevent any virus from negatively affecting your system. However, the problem with this approach is that it also prevents you from installing new software, unless you unlock it. If you are a regular user who does not often install new software, this is the perfect option for you. With this following link you will find the full instructions how to lock down and immunize your Windows.
 Another way to
protect your Windows is to use the Sandboxie software
mentioned above. Not only does this software build a
fortress around your browser so that your surfing experience cannot affect any other part
of your computer, you can also use it to create a fortress wall around programs
you are not certain about. For example if your friend sent you a file with the
naughty or potentially dangerous .exe extension (as explained
here) and you
are not sure whether the email was sent due to a virus that your friend had caught.
Any time you are not certain about a file or program you can use Sandboxie to
test view/run it.
Another way to
protect your Windows is to use the Sandboxie software
mentioned above. Not only does this software build a
fortress around your browser so that your surfing experience cannot affect any other part
of your computer, you can also use it to create a fortress wall around programs
you are not certain about. For example if your friend sent you a file with the
naughty or potentially dangerous .exe extension (as explained
here) and you
are not sure whether the email was sent due to a virus that your friend had caught.
Any time you are not certain about a file or program you can use Sandboxie to
test view/run it.
A good firewall will prevent hackers from getting into your computer externally. If your system is not well protected there are programs out there which search the net for open ports and inform their owners when they have found a vulnerability. The Windows firewall is generally good but not the best. A few firewalls are suggested through the Lock Down and Immunize your Windows link above, one in particular being free: Jetico Personal Firewall. Unfortunately the free version made my entire system crash occasionally so I went ahead and bought the full version, which wasn't that expensive. It is rated much better than Windows' firewall and has a handy feature whereby it can show you exactly how much data is being transferred to and from your computer via the internet (in terms of number of packets and number of kilobytes), and in another window breaks down how many bytes are being transferred by which programs. In this way you can really get good control over your computer, thereby deactivate or research any programs which are suspiciously transferrng data.
And lastly, it is generally a good idea to keep such commonly used software as iTunes, QuickTime, RealPlayer, Adobe Acrobat, and Adobe Reader; as well as various instant messaging clients such as AIM, MSN, Yahoo!, and the VoIP client Skype up to date because they are often used as entry points by hackers.
Monitor Your System
Scotty's WinPatrol is similar to Window's Task Manager but with more features, and there has been times when I found a process running which did not appear in Task Manager. WinPatrol performs several functions:
-
 if a new program is installed (whether you know about
it or not) and starts to make changes to Windows' brain (registry), it blocks it, warns
you about it, and gives you the opportunity to remedy the situation. The
problem is that sometimes there is a significant delay before blocking it.
Nevertheless it is a good feature and the more backup systems you have, the
better
if a new program is installed (whether you know about
it or not) and starts to make changes to Windows' brain (registry), it blocks it, warns
you about it, and gives you the opportunity to remedy the situation. The
problem is that sometimes there is a significant delay before blocking it.
Nevertheless it is a good feature and the more backup systems you have, the
better -
like the Task bar it shows you all the processes running on your system. You may know of one program running on your computer, but not realise it is running several processes (essentially mini or sub-programs). Not to mention all the other processes currently running on your system - whether part of Windows, some hidden program you don't know about, or a virus. Below in this section is explained how to analyse each process and deal with it.
-
it has many other features which you can check out, and it's free! But you can pay a little bit of money to have the more beefed-up version with added goodies.
As the WinPatrol site explains: "99% of these threats all have one thing in common - they are set to execute from one or more of the "Run" keys in the Registry. To protect against these silent additions: Add a Startup Monitor to your Layered Protection."
Another program which can offer similar protection to the first point above is Spybot's TeaTimer. It runs in the background and immediately blocks and warns you if some program is trying to make any changes to your registry (basically the inner workings of Windows' brain). However, I found that this subprogram of Spybot hogged more resources than my liking. You can also find other such programs on the internet which use much less resources and are as effective.
How to Inspect and Deal with Unwanted Processes
Whether you use the Task Manager or Scotty's WinPatrol, it is good to know what is running on your system and how to deal with it. System Idle Process is basically your system idling and represents the unused resources. Therefore, if it reads 99%, it means that only 1% of your CPU is being used. This is normal and healthy if you are not running a demanding program. If it reads 90%, it means that 10% of your CPU
 HIV Virus |
(your processor - the thing that does all the work and computing on your computer) is being used by one or more programs. If you suspect that your computer should not be using 10% of its horsepower because you are not performing any demanding tasks, it is time to analyse your processes. For example, lets say process1 is using 5% and process2 another 5% (adding up to the 10% your computer is using). You can analyse each of these processes to understand what programs control them. Let us take the common Windows process svchost.exe. To the right of this process in the Processes tab you can see the percentage of the computer's CPU capacity used by the process, and to the right of that the MEM usage (how much RAM or memory it is using).
Once you've found a process you are suspicious about and would like to learn more about, just google it. For our example above you would simply google "svchost.exe". Whatever process you google, I often find many websites which explain what exactly that process does. Sometimes a site will inform you that that particular process can be a virus which purposefully names its process that way to masquerade itself as a normal Windows program, and provide you with detailed instructions how to remove it from your system. It is these masquerading processes which can escape undetected by many virus protection programs, for which reason it is good for you to learn how to dissect your system and learn everything about it. These websites can branch out to tech forums, or you can hunt them down yourself, and really learn how to control and monitor your system.
 Flu Virus |
But be aware because I've recently noticed many new such process-describing websites which seemed to copy the content of the well established ones and flash scary messages inciting you to download their software to run a complete scan of your system. Be aware because such software can easily be adware or even a virus!! The well established ones (such as www.liutilities.com and www.processlibrary.com/) usually offer useful information and don't try too hard to push something on you. You've already got all the scanning software you need from these pages - so don't download any bells and whistles and stick to studying the individual components only. Read away until you have a firm understanding and confidence in your system, and if you have the time, study every single process on your system to make sure it is nice and clean. You can even write down a list of all the processes you've examined, copying from the above website information regarding them. This way, you can always quickly refer to this list of "approved processes" in case one pops up in the future which you do not remember or recognise (so you do not have to study all the processes over again).
As mentioned in my Computer Tips pages I like to have my Task Manager running all the time (does not use much system resources) so that I can see how much of my CPU is being used. If it jumps high while I am not doing anything special, I immediately examine which process is using such a high percentage of CPU.
But another thing I like to monitor is my harddrive.
 All
laptops and desktop computers should come equipped with a little light somewhere
showing when your harddrive is being used. For example when you open up a new
program or copy a big file from one part of your computer to another. When data
is being drawn or copied from or to your harddrive, this light flickers. If I notice the
light is flickering while I am not doing anything special, I am
immediately suspicious. For example, what if some virus was scanning your computer looking
for your credit card information to send it somewhere by email? You get
my point.
All
laptops and desktop computers should come equipped with a little light somewhere
showing when your harddrive is being used. For example when you open up a new
program or copy a big file from one part of your computer to another. When data
is being drawn or copied from or to your harddrive, this light flickers. If I notice the
light is flickering while I am not doing anything special, I am
immediately suspicious. For example, what if some virus was scanning your computer looking
for your credit card information to send it somewhere by email? You get
my point.
For this I found a hard disk monitor dkharddrive-light. I couldn't find who developed this software but if you google it you will find many sites which offer this free download, such as cnet. This is a light program which monitors everything which is happening on your harddrive. My harddrive light was flashing too often so I used this software to research what programs were using it. Fortunately it was no virus but I discovered I had many logging programs I did not need, so I turned them off. If many programs are using your harddrive for storing unnecessary information, it will slow down all your other programs, because your harddisk can spin only so fast or retrieve or copy so much information.
Don't be afraid of your system. Learn it, control it, and sleep well at night.
|
|
Test your security with these free systems:
Once you've completely cleaned and protected your computer, for your personal assurance you could test its security.
|
Online port and file sharing test – free online test that mimics a hacker through your internet connection. Totally safe and very revealing! PC Security Test – Download this free software and let it scan your system’s defenses. |
If you received less than perfect or favourable results, read further, because your finances and personal security may depend on it!
Below you will see my personal results for the above two tests.
Internet connection test results (file sharing):
|
|
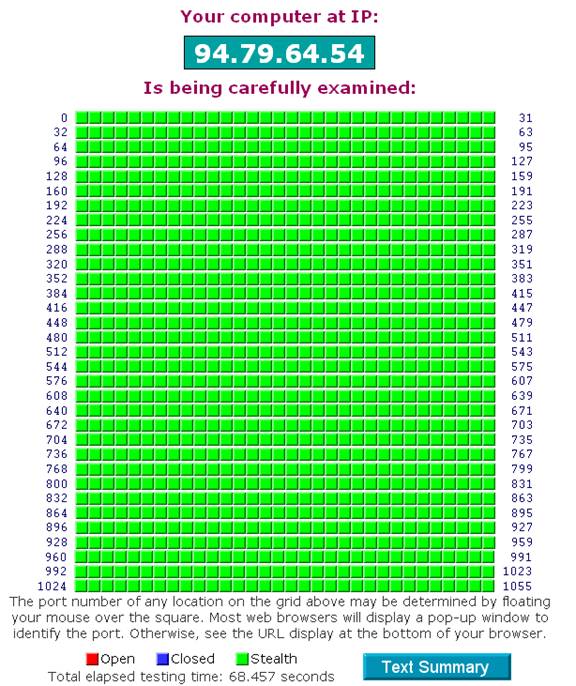
Your Internet port 139 does not appear to exist!
|
|
|
Unable to connect with NetBIOS to your computer. |
Common ports:
Your system has achieved a perfect "TruStealth" rating.
Not a single packet — solicited or otherwise — was received from your system
as a result of our security probing tests. Your system ignored and refused to
reply to repeated Pings (ICMP Echo Requests). From the standpoint of the passing
probes of any hacker, this machine does not exist on the Internet. Some
questionable personal security systems expose their users by attempting to
"counter-probe the prober", thus revealing themselves. But your system wisely
remained silent in every way. Very nice.
All service ports (first 1056):
Back Up Your System
Now that you've spent all this time perfecting a beautiful
system, making it impenetrable against viruses and you are tickled with glee,
you accidentally spill your cup of coffee into your laptop keyboard, it drops
out of your backpack or other annoying calamity and you lose everything! In this
case its good to have a solid backup of your entire system. But before you do
this I would suggest you read the section below to
 tweak it further and turn it
into a real powerhorse. Perfect it until you are totally happy with it, because
some work will be involved in backing it up, so you might as well go an extra yard
and backup a perfectly tuned system. You can do a
basic Windows system backup, or better
yet perform a full computer backup
using such software as Acronis
or Norton Ghost.
I heard that Acronis was better, and you can download the program for free,
perhaps only paying when you actually need to restore your backup.
tweak it further and turn it
into a real powerhorse. Perfect it until you are totally happy with it, because
some work will be involved in backing it up, so you might as well go an extra yard
and backup a perfectly tuned system. You can do a
basic Windows system backup, or better
yet perform a full computer backup
using such software as Acronis
or Norton Ghost.
I heard that Acronis was better, and you can download the program for free,
perhaps only paying when you actually need to restore your backup.
Before you backup it might be a good idea to temporarily move (such as to an external harddrive or writeable DVD) stuff that you don't need to backup as part of your system, such as folders full of pictures. Because it will only make your backup file larger.
Once you have cleaned up your computer and perfected it, create your massive backup file. Mine worked out to about 50 gigabytes. You can then store this on an external harddrive somewhere AWAY from your computer. This way, if someone steels it or breaks it, you only need to get a new computer or part (such as the burned out hard drive) and restore your beautifully tweaked system in all its glory. But since I've had bad experience with external hard drives and DVDs (you can break up the 50 gig backup file into parts and save them individually onto separate DVDs), and because for my business I cannot afford to spend a month setting up a new system, I've found a good site where I can backup my important files online (recommended to me by the experts and internet reviews). Something like 50 bucks a year for unlimited space, and you can regularly backup individual and important files on your computer, automatically whenever they change. 50 bucks is certainly worth it for me to avoid the hassle of setting up my entire, perfect system all over again.
Conclusion
 you might be better off just buying a Macintosh. The hackers and phishers and spywarers don't usually bother with this operating system because
it has such a small market share. Linux, a free system, is also another option,
but I found it has a potentially annoying learning curve. Google is apparently
also coming out with its own operating system but one which is designed from the
ground up with internet in mind. I feel this could offer great potential.
you might be better off just buying a Macintosh. The hackers and phishers and spywarers don't usually bother with this operating system because
it has such a small market share. Linux, a free system, is also another option,
but I found it has a potentially annoying learning curve. Google is apparently
also coming out with its own operating system but one which is designed from the
ground up with internet in mind. I feel this could offer great potential.
|
|
Some websites and articles I have accumulated concerning this subject:
http://www.techsupportalert.com/pc/security-tools.html (free security tools – lots of other stuff on their main page)
http://news.bbc.co.uk/2/hi/technology/7675882.stm – now can spread to ppcs (palmpilots and pocket pcs)
http://news.bbc.co.uk/2/hi/technology/7681534.stm – keyboard sniffing using radio waves etc. : One attack was shown to work over a distance of 20 metres. In their work the researchers used a radio antenna to "fully or partially recover keystrokes" by spotting the electromagnetic radiation emitted when keys were pressed.
http://news.bbc.co.uk/2/hi/technology/7701227.stm - Sinofall Trojan virus article about “drive-by downloads”
Checking for/Help with Hijackware
http://aumha.org/a/parasite.htm
http://aumha.org/a/quickfix.htm
http://aumha.net/viewtopic.php?t=5878
http://wiki.castlecops.com/Malware_Removal_and_Prevention:_Introduction
http://mvps.org/winhelp2002/unwanted.htm
http://inetexplorer.mvps.org/data/prevention.htm
http://inetexplorer.mvps.org/tshoot.html
http://www.mvps.org/sramesh2k/Malware_Defence.htm
http://defendingyourmachine2.blogspot.com/
http://www.elephantboycomputers.com/page2.html#Removing_Malware
When all else fails, HijackThis v2.0.2
(http://aumha.org/downloads/hijackthis.exe)
is the preferred tool to use (in
conjuction with some other utilities). HijackThis will NOT fix anything on
its own, but it will help you to both identify and remove any
hijackware/spyware with assistance from an expert. **Post your log to
http://spywarehammer.com/simplemachinesforum/index.php?board=10.0,
http://forums.spybot.info/forumdisplay.php?f=22,
http://aumha.net/viewforum.php?f=30, or another appropriate forum for review
by an expert in such matters, not here.**
-------------
Here's a letter I wrote to all my friends after I heard about this latest scam. You can send it to your friends as well and hopefully educate the international community to make the world a smoother running place.
latest scan – beware!
I'm sure you get such similar warnings all the time, but not one this unique!!!
So get this, I have a friend living in LA. He owns a business, someone calls him up pretending to be a customer. They might record the conversation, practice his tone and personality, research his business and private life. Once they are confident they are well practiced enough and have gained enough information, they call up his mother in Canada, claim they are him and say he is calling from jail and need some 3000$ to bail him out. This actually happened my friends (and she paid!!). A new dimension in scam. Forward this email to everyone and please lets all get educated about the internet.
While we're educating people, please note that many of these forward requests are scams in themselves. That if you forward some mail to 9 friends you will be lucky for a year. Or for each person you forward mail to 3 cents will be donated by the Red Cross to some girl lying on her death bed in a hospital. THIS IS TOTAL BS!! The Red Cross or any other organization has no way of knowing how many people you forward an email to but it is a simple ploy by spammers because when most people forward emails they throw the email addresses into CC, which is Carbon Copy, and hence everyone's email address is exposed in the forwarded email, which is circulating the internet in ever increasing numbers (and which the spammers hope will eventually circulate back to them so they could sell the email addresses or use them). If you really want to forward an email to many people you should throw their emails into BCC, which is Blind Carbon Copy, meaning the addresses are buried and hidden in the email. But even for this there is special software which can unearth it and which spammers will certainly be using. So please use careful discretion when forwarding mass emails. Spammers are crippling the internet and honest businesses. Because of spammers I often have problems that my emails do not get to my customers or translators, so it is harming my business.
Also, some 30 to 60% of personal computers in the world are infected by viruses and botnets which run in the background and are used by criminal organizations to shut down organizations and even governments. Here's one article if you do not believe me:
http://news.bbc.co.uk/2/hi/technology/8026964.stm
Just google "botnets news" or something like that. As a PC
user and citizen of this world you should take responsibility for your machine
and not let criminal forces use it. The article above indicates that the
Please forward this and educate the international community.
I've prepared some instructions how to virus protect your computer at:
http://001yourtranslationservice.com/computer-tips/protecting-your-computer.htm
Happy computering!
|
|
------------------------
Still to do:
< add to Perfect Email about the need to clean system and why your emails might be blocked or thrown into your recipient’s junkbox (which most people don’t check) if a virus is detected on your system
< if you use any of these tools and they point to some .exe file running among your processes <point to explanation> , you can research it on the net. Processlibrary seems pretty good, but don’t be afraid to search other sites as well, or even forums where they talk about it, simply by searching for that .exe file in google and see what comes up.
< add: thought it was funny that superspyware blabblab found only one Trojan (after I did a scan with Spybot, and I don’t surf HongKong porn etc.) was a cookie which I just allowed to install with my Panda scan…
< make reference to my email program (Email Solution) somewhere?
< if you want to make changes to the Hosts file, make sure to temporarily turn off Avorax (double click on the Avorax icon in the system tray, click on the On/Off button to temporarily turn it off)
- add to previous computer tips cleaning page: about the guy from techsupportalert <mention that mention later?> who surfed the seediest Hong Kong website to infect his computer as much as possible, and then used it to test the various antispyware software. I was shocked to find out that my beloved S&D found and removed only 5-8% of these infections…
- for locking down the computer, suggest saving the html file to computer so that don’t have to remember everything. Save the file to my web and link to him, as a backup… Upload all the files to 001 as backup..
- when Arovax asks you to accept, if you trust the software (like Firefox, which is now even more protected with all the addons and other security you have added), simply select Handle As and choose the appropriate setting (Trusted Application Zone, Web Browser, etc.), and make sure the “Remember this choice” <same> is selected to make sure the firewall will not bother you with it again.
- after adding all these things you will notice a reduction in available ram <link to explanation>, by perhaps 150 MB, but this should be an acceptable cost to have such a high degree of security. You can always buy more ram…
- one of the adaware removal programs I ran on my system copied over top of my protective Hosts file with the empty default version, so double check your file once you’re done with all these procedures.
- add comment to perfect email about checking the spambox (less than perfect, boohoo, but important if you do not want to lose potential customers). In any case, I can look this box when I have time, many people do go through the verification process, and I don’t get ANY spam in my inbox when I am busy.
- unfortunately have to unlock I believe every time you want to install new software etc., and then relock it, both of which requires restarting your computer, but a worthy price to pay if you want total protection.
- make sure to upload my new system’s backup file.
Compare the results of the online test above < to the results I received from this website after I installed all this free software:
< say how individual programs are lean and mean and do not interfere with system resources, like such single and expensive programs would (let alone that they simply do not offer the same security)
< point form showing what my simple steps will accomplish on their system
< link somewhere to previous computer tips page – how to clean it up and all that.
< Marketing text and scare tactics at top. – copy some scare text from the bottom.
< did I mention about adding security pass to harddrive (before Windows login) and using a non-administration account when hooking up to public internet or cafes?
More
computer tips
How to Set up and Properly Secure WordPress
Introduction to PHP
Internet
Connection While You Travel

KENAX
Translation Agency and
Outsourcing
(programming work, graphics design, full list of outsourcing)
Copyright © KENAX, by Karel Kosman - All Rights Reserved Worldwide.